Bless Network Litepaper
Decentralized applications (dApps) built exclusively on blockchain networks surrender both the right for their users to provide compute power to them directly, as well as the right to use a different verification and consensus method to what is provided by the underlying blockchain network, leading to monolithic, inefficient and unscalable applications, tethered to one verification method and one homogenous network of nodes for many different types of computation.
Bless addresses both issues with our network-neutral application (nnApp) framework enabling users to provide compute power simply by opening the application; through what we refer to as our ‘nestled node’ infrastructure. This enables all nnApps to draw upon their own users’ devices to provide compute resources - and reward them for doing so. Whilst applications may opt for governance and token workloads to remain on Ethereum or any other blockchain, and data availability workloads on Celestia or EigenLayer, intensive computations for use-cases like machine learning, AI interfaces and gaming will run through the fully decentralized, faster and efficient off-chain environment provided by Bless - all via the application’s own user base. This results in the computational support for these applications directly scaling with the growth in the number of their users, with more users resulting in more community-provided computing power.
This represents a shift in how users experience the internet, where for the first time, nose-to-tail decentralization will be possible for applications and their users without the costs, complications, and performance issues frequently associated with decentralized networks. As a result of this, decentralized applications can leverage centralized speeds with the benefits of decentralization, and off-chain heavy computations with the benefits of on-chain finality.
In the Bless Network, an application’s tasks are strategically distributed amongst node groups, tailored to their computational strengths. Each node group is formed and dissolved for each workload, ensuring that the most efficient nodes are selected for each workload in an application.
This approach contrasts with traditional decentralized networks, which often do not differentiate between nodes based on hardware specifications, and rely heavily upon institutional providers where more power equates to more work. As a result, these networks face limitations in capability diversity and risk centralized control in node operations.
Bless prioritizes orchestration, aligning tasks with the most suitable nodes. For intensive tasks, like machine learning, high-performance servers are engaged. For lighter duties, such as data retrieval and analytics, desktop computers, laptops and mobile phones are perfectly capable of achieving the same level of performance. Nestled nodes are only allocated tasks that they are able to handle, with the wider Bless network providing support where nestled nodes are unable to meet the hardware requirements. You can see how the wider Bless operates below.
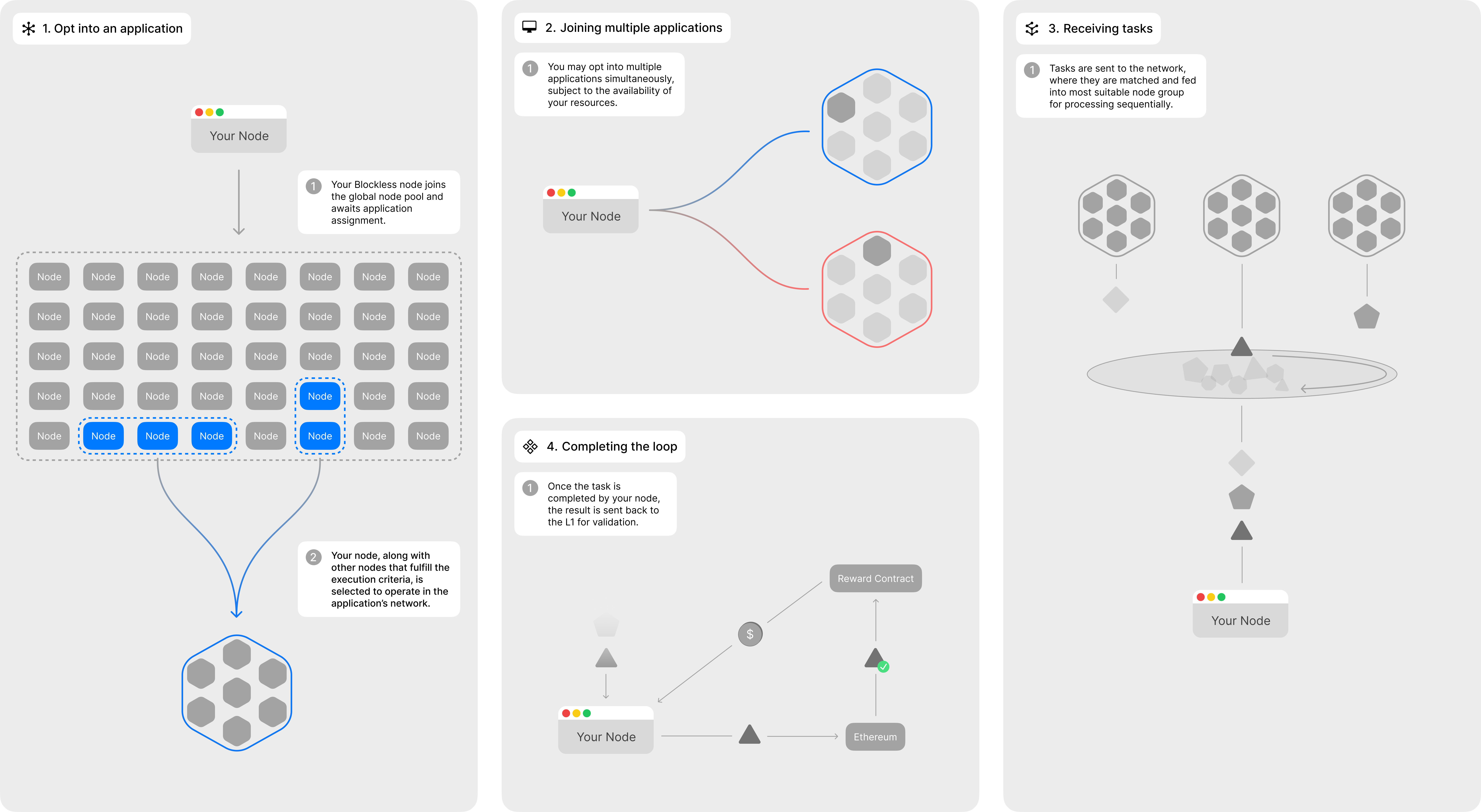
When deploying an application on Bless, developers can specify the number of nodes they require and Bless dynamically selects the optimal nodes from the pool available, taking into account geolocation, hardware specifications and performance scoring. Once a group of nodes has been selected, each one downloads the necessary files as WASM (WebAssembly) binary code and executes them within our secure runtime environment. Post-execution, the network validates each task based on the application’s verification requirements. The results are then securely stored on the preferred blockchain(s). This blockchain record-keeping is key when it comes to rewarding participating nodes, creating a fair and transparent incentive mechanism.
To ensure the security of the network, and to create a seamless experience for nnApp users, Bless will leverage a Proof of Stake (PoS) model, where stakers of the Bless token enable the pool of nestled node-runners to provide compute resources automatically, whilst also enabling the node-runners using the dedicated Bless node software (downloadable as a desktop application and/or a Chrome Extension) to power multiple applications at once.
The Bless Network represents a vital step forward in the world of decentralized networks, where efficiency and interoperability are extended not to specific networks, or applications, but to each and every workload within those applications, all supported by the people that use them.
To better understand how this is all possible, we’ve broken down some of the key technical components below.
If users can provide compute resources to applications simply by using them, the pool of user devices (nodes) will naturally vary in hardware specifications capacity to complete computations. There may be dedicated machines capable of ML training, desktop computers primarily used for gaming or video editing, or laptops and smartphones used for browsing the web and conducting various on-chain activities. Our Dynamic Resource Matching is a comprehensive sorting mechanism used to categorize these devices and match them individually to the most suitable computational task.
Each computational request in the network initiates a selection process to identify online nodes meeting the task’s basic requirements. This step ensures that less capable devices, such as home PCs, are not burdened with complex computations like generating Zero-Knowledge proofs. It also ensures that lighter tasks aren’t allocated to large servers if smaller devices can handle the workload more efficiently.
Further refinement is achieved through a Simulated Annealing (SA)-based evaluation, pinpointing the most reliable and capable devices for specific computations. This evaluation considers factors such as response time and hardware specifications and simulates how each device/node would perform for a particular computation. The evaluation process also takes into account the historical performance of a node, resulting in poorly-performing nodes receiving a lower ranking and receiving less work as a result.
These coordinated steps form part of how Bless efficiently manages various computations whilst upholding stringent standards for the security, reliability, and performance of the network.
To mitigate the risk of malicious behavior on the network, Bless employs a randomized distribution algorithm for task allocation. This strategy addresses a potential vulnerability where bad actors with abundant compute resources who are familiar with the dynamic resource matching described in the section above, might anticipate and exploit their likely allocation of compute-intensive tasks (like ML inference). The algorithm utilizes a Greco-Latin square distribution method, ensuring an even and resource-aware task distribution among the selected nodes. That means that within the group of optimal nodes selected for any particular task, only some are chosen. This approach prevents nodes from predicting their receipt of any particular task, enhancing the integrity of the network.
In order to maintain a stable network, Bless incorporates a Web-Assembly (WASM) secure runtime to establish a distinct separation between the computational tasks and the broader activities of the node device. This secure runtime ensures that specific system resources (like CPU, GPU and RAM) are exclusively allocated for Bless Network applications. As a result, even when the node device is engaged in resource-intensive activities like video editing, streaming or gaming, the performance and efficiency of Bless applications remain unaffected.
Additionally, this secure runtime maintains confidentiality and integrity by shielding the node machine from accessing or altering the runtime’s internal processes. It also safeguards against excessive resource consumption and unauthorized access to sensitive data by the application.
It’s worth noting for developers that Web-Assembly’s versatile runtime enables Bless to support applications built on a wide range of mainstream programming languages, including Python, JavaScript, Go, and Rust, thus broadening its accessibility, and making it easy for developers to integrate their work.
Bless goes beyond randomized distribution and WASM secure runtime in ensuring security and fault tolerance, by offering applications the choice to implement an additional verification mechanism for each computational task. This modular approach enables the processing of a diverse range of computations efficiently, based on the needs of each computation.
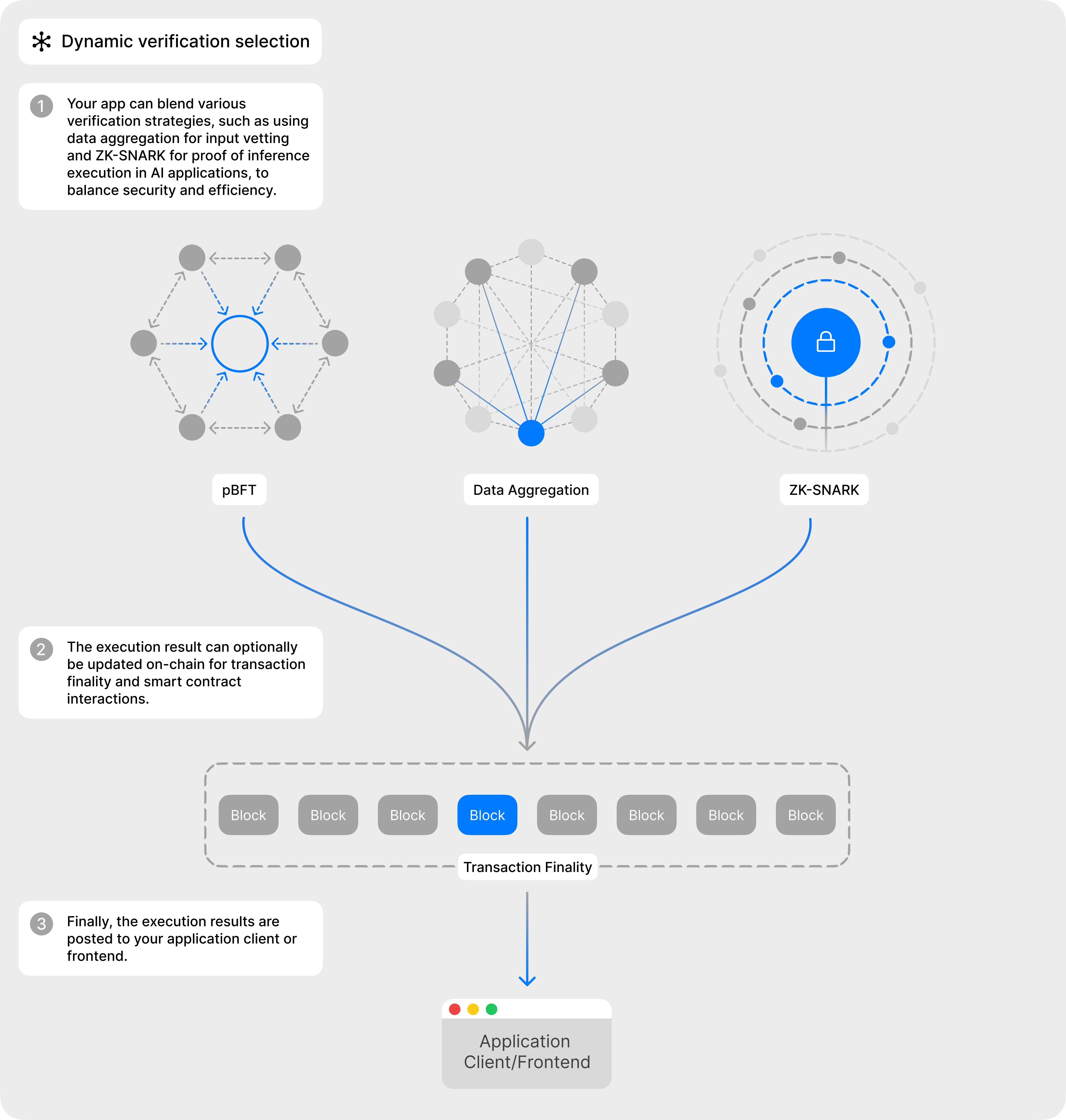
For example, in tasks like retrieving price feeds for Bitcoin, Bless nodes can collate their findings and calculate a weighted average, ensuring an accurate and reliable result. For tasks that yield binary (yes/no) outcomes, employing consensus algorithms like Practical Byzantine Fault Tolerance (pBFT) or RAFT for node voting is more suitable, ensuring optimal decision-making. Different computations necessitate different methods of consensus and verification, and Bless serves as both the orchestrator and computational layer for these.
To verify the results and that the computations were carried out correctly, Bless nodes can also generate Zero-Knowledge Proofs as a final verification step. This multi-layered and modular approach to verification ensures that applications on Bless are backed by robust and sound computations, enhancing trust and reliability within the network.
Our testnet, and the first examples of decentralized applications powered by their own users from frontend to backend, will be released in Q4 2024. In the meantime, join us here.